A simple computer network may be constructed from two computers by adding a network
adapter (Network Interface Controller (NIC)) to each computer and then connecting them
together with a special cable called a crossover cable. This type of network is useful for
transferring information between two computers that are not normally connected to each
other by a permanent network connection or for basic home networking applications.
Alternatively, a network between two computers can be established without dedicated
extra hardware by using a standard connection such as the RS-232 serial port on both
computers, connecting them to each other via a special crosslinked null modem cable.
Practical networks generally consist of more than two interconnected computers and
generally require special devices in addition to the Network Interface Controller that each
computer needs to be equipped with. Examples of some of these special devices are hubs,
switches and routers.
Thursday, November 13, 2008
Building a simple computer network
Tuesday, November 11, 2008
Routers
Routers are the networking device that forward data packets along networks by using
headers and forwarding tables to determine the best path to forward the packets. Routers
work at the network layer of the TCP/IP model or layer 3 of the OSI model. Routers also
provide interconnectivity between like and unlike media (RFC 1812) This is
accomplished by examining the Header of a data packet, and making a decision on the
next hop to which it should be sent (RFC 1812) They use preconfigured static routes,
status of their hardware interfaces, and routing protocols to select the best route between
any two subnets. A router is connected to at least two networks, commonly two LANs or
WANs or a LAN and its ISP's network. Some DSL and cable modems, for home use,
have been integrated with routers to allow multiple home computers to access the
Internet.
headers and forwarding tables to determine the best path to forward the packets. Routers
work at the network layer of the TCP/IP model or layer 3 of the OSI model. Routers also
provide interconnectivity between like and unlike media (RFC 1812) This is
accomplished by examining the Header of a data packet, and making a decision on the
next hop to which it should be sent (RFC 1812) They use preconfigured static routes,
status of their hardware interfaces, and routing protocols to select the best route between
any two subnets. A router is connected to at least two networks, commonly two LANs or
WANs or a LAN and its ISP's network. Some DSL and cable modems, for home use,
have been integrated with routers to allow multiple home computers to access the
Internet.
Hubs
hub contains multiple ports. When a packet arrives at one port, it is copied to all the ports of the hub. When the packets are copied, the destination address in the frame does not change to a broadcast address. It does this in a rudimentary way, it simply copies the data to all of the Nodes connected to the hub.
Switches
Switches are a marketing term that encompasses routers and bridges, as well as devices that may distribute traffic on load or by application content (e.g., a Web URL identifier). Switches may operate at one or more OSI layers, including physical, data link, network, or transport (i.e., end-to-end). A device that operates simultaneously at more than one of these layers is called a multilayer switch.
Overemphasizing the ill-defined term "switch" often leads to confusion when first trying to understand networking. Many experienced network designers and operators recommend starting with the logic of devices dealing with only one protocol level, not all of which are covered by OSI. Multilayer device selection is an advanced topic that may lead to selecting particular implementations, but multilayer switching is simply not a realworld design concept.
Overemphasizing the ill-defined term "switch" often leads to confusion when first trying to understand networking. Many experienced network designers and operators recommend starting with the logic of devices dealing with only one protocol level, not all of which are covered by OSI. Multilayer device selection is an advanced topic that may lead to selecting particular implementations, but multilayer switching is simply not a realworld design concept.
Bridges
Network bridge connects multiple network segments at the data link layer (layer 2) of the OSI model. Bridges do not promiscuously copy traffic to all ports, as hubs do. but learns which MAC addresses are reachable through specific ports. Once the bridge associates a port and an address, it will send traffic for that address only to that port. Bridges do send broadcasts to all ports except the one on which the broadcast was received.
Bridges learn the association of ports and addresses by examining the source address of frames that it sees on various ports. Once a frame arrives through a port, its source address is stored and the bridge assumes that MAC address is associated with that port. The first time that a previously unknown destination address is seen, the bridge will forward the frame to all ports other than the one on which the frame arrived.
Bridges come in three basic types :
1. Local bridges: Directly connect local area networks (LANs)
2. Remote bridges: Can be used to create a wide area network (WAN) link between
LANs. Remote bridges, where the connecting link is slower than the end
networks, largely have been replaced by routers.
3. Wireless bridges: Can be used to join LANs or connect remote stations to LANs.
Bridges learn the association of ports and addresses by examining the source address of frames that it sees on various ports. Once a frame arrives through a port, its source address is stored and the bridge assumes that MAC address is associated with that port. The first time that a previously unknown destination address is seen, the bridge will forward the frame to all ports other than the one on which the frame arrived.
Bridges come in three basic types :
1. Local bridges: Directly connect local area networks (LANs)
2. Remote bridges: Can be used to create a wide area network (WAN) link between
LANs. Remote bridges, where the connecting link is slower than the end
networks, largely have been replaced by routers.
3. Wireless bridges: Can be used to join LANs or connect remote stations to LANs.
Repeaters
repeater is an electronic device that receives a signal and retransmits it at a higher level or higher power, or onto the other side of an obstruction, so that the signal can cover longer distances without degradation.
Because repeaters work with the actual physical signal, and do not attempt to interpret the data being transmitted, they operate on the Physical layer, the first layer of the OSI model.
Because repeaters work with the actual physical signal, and do not attempt to interpret the data being transmitted, they operate on the Physical layer, the first layer of the OSI model.
Network Interface Cards
A network card, network adapter or NIC (network interface card) is a piece of computer hardware designed to allow computers to communicate over a computer network. It provides physical access to a networking medium and often provides a lowlevel addressing system through the use of MAC addresses. It allows users to connect to each other either by using cables or wirelessly.
Basic Hardware Components for Computer Network
All networks are made up of basic hardware building blocks to interconnect network nodes, such as Network Interface Cards (NICs), Bridges, Hubs, Switches, and Routers. In addition, some method of connecting these building blocks is required, usually in the form of galvanic cable (most commonly Category 5 cable). Less common are microwave links (as in IEEE 802.11) or optical cable ("optical fiber").
Basic Hardware Components for Computer Network :
Network Interface Cards
Repeaters
Hubs
Bridges
Switches
Routers
Basic Hardware Components for Computer Network :
Network Interface Cards
Repeaters
Hubs
Bridges
Switches
Routers
Monday, November 10, 2008
By protocol
Computer network_(part2)
By protocol
By protocol
Computer networks may be classified according to the communications protocol that is being used on the network. See the articles on List of network protocol stacks and List of network protocols for more information. For a development of the foundations of protocol design see Srikant 2004 and Meyn 2007
Wikipedia.com
By network topology
Computer networks may be classified according to the network topology upon which the network is based, such as Bus network, Star network, Ring network, Mesh network, Starbus network, Tree or Hierarchical topology network, etc.
Network Topology signifies the way in which intelligent devices in the network see their logical relations to one another. The use of the term "logical" here is significant. That is, network topology is independent of the "physical" layout of the network. Even if networked computers are physically placed in a linear arrangement, if they are connected via a hub, the network has a Star topology, rather than a Bus Topology. In this regard the visual and operational characteristics of a network are distinct; the logical network topology is not necessarily the same as the physical layout.
Network Topology signifies the way in which intelligent devices in the network see their logical relations to one another. The use of the term "logical" here is significant. That is, network topology is independent of the "physical" layout of the network. Even if networked computers are physically placed in a linear arrangement, if they are connected via a hub, the network has a Star topology, rather than a Bus Topology. In this regard the visual and operational characteristics of a network are distinct; the logical network topology is not necessarily the same as the physical layout.
Author : KAREN
By functional relationship (Network Architectures)
Computer networks may be classified according to the functional relationships which exist between the elements of the network, for example Active Networking, Client-server and Peer-to-peer (workgroup) architectures.
Author : KAREN
By connection method
Computer networks may be classified according to the hardware technology that is used to connect the individual devices in the network such as Optical fiber, Ethernet, Wireless LAN, HomePNA, or Power line communication.
Ethernets use physical wiring to connect devices. Often, they employ the use of hubs, switches, bridges, and routers.
Wireless LAN technology is built to connect devices without wiring. These devices use a radio frequency to connect.
Ethernets use physical wiring to connect devices. Often, they employ the use of hubs, switches, bridges, and routers.
Wireless LAN technology is built to connect devices without wiring. These devices use a radio frequency to connect.
Author : KAREN
By scale
Computer networks may be classified according to the scale: Personal area network (PAN), Local Area Network (LAN), Campus Area Network (CAN), Metropolitan area network (MAN), or Wide area network (WAN). As Ethernet increasingly is the standard interface to networks, these distinctions are more important to the network administrator than the end user. Network administrators may have to tune the network, based on delay that derives from distance, to achieve the desired Quality of Service (QoS). The primary difference in the networks is the size.
Controller Area Networks are a special niche, as in control of a vehicle's engine, a boat's electronics, or a set of factory robots.
Controller Area Networks are a special niche, as in control of a vehicle's engine, a boat's electronics, or a set of factory robots.
Author : KAREN
Computer network_(part2)
A computer network is an interconnection of a group of computers. Networks may be classified by what is called the network layer at which they operate according to basic reference models considered as standards in the industry such as the four-layer Internet Protocol Suite model. While the seven-layer Open Systems Interconnection (OSI) reference model is better known in academia, the majority of networks use the Internet Protocol Suite (IP) as their network model.
By scale
By connection method
By functional relationship (Network Architectures)
By network topology
By protocol
By scale
By connection method
By functional relationship (Network Architectures)
By network topology
By protocol
Author : KAREN
Sunday, November 2, 2008
OSI Model
The Open System Interconnection (OSI) reference model provides a set of international rules and standard to allow any system obeying these protocols to communicate with other systems that use them. These protocols are arranged in seven separate but interconnected layers, each dealing with a different aspect of the communication. Among other things, this allows hardware, like routers and firewalls, to focus on the particular aspect of communication that applies to them, and ignore other parts.
The seven OSI layers are as :
The seven OSI layers are as :
1. Physical layer
This layer deals with the physical connection between two points. This is the lowest layer, and its major role is communicating raw bit streams. This layer is also responsible for activating, maintaining, and deactivating these bit-stream communications.
2. Data link layer
This layer deals with actually transferring data between two points. The physical layer takes care of sending the raw bits, but this layer provides high-level function, such as error correction and flow control. This layer also provides procedures for activating, maintaining, and deactivating data-link connections.
3. Network layer
This layer works as a middle ground, and its key role is to pass information between lower and higher layers. It provides addressing and routing.
4. Transport layer
This layer provides transparent transfer of data between systems. By providing a means to reliably communicate data, this layer allows the higher layers to worry about other things besides reliable or cost-effective means of data transmission.
5. Session layer
This is layer responsible for establishing and then maintaining connections between network applications.
6. Presentation layer
This layer is responsible for presenting the data to applications in a syntax or language they understands. This allows for things like encryption and data compression.
7. Application layer
This layer is concerned with keeping track of the requirements of the application.
This layer deals with the physical connection between two points. This is the lowest layer, and its major role is communicating raw bit streams. This layer is also responsible for activating, maintaining, and deactivating these bit-stream communications.
2. Data link layer
This layer deals with actually transferring data between two points. The physical layer takes care of sending the raw bits, but this layer provides high-level function, such as error correction and flow control. This layer also provides procedures for activating, maintaining, and deactivating data-link connections.
3. Network layer
This layer works as a middle ground, and its key role is to pass information between lower and higher layers. It provides addressing and routing.
4. Transport layer
This layer provides transparent transfer of data between systems. By providing a means to reliably communicate data, this layer allows the higher layers to worry about other things besides reliable or cost-effective means of data transmission.
5. Session layer
This is layer responsible for establishing and then maintaining connections between network applications.
6. Presentation layer
This layer is responsible for presenting the data to applications in a syntax or language they understands. This allows for things like encryption and data compression.
7. Application layer
This layer is concerned with keeping track of the requirements of the application.
When data is communicated through these protocols, it’s sent in small pieces called packets. Each packet contains implementations of these protocols in layers. Starting from the application layer, the packet wraps these protocol in layers. Starting from the application layer, the packet wraps the presentation layer around that data, which wraps the session layer around that, which wrap the transport layer, and so forth. This process is called encapsulation. Each wrapped layer contains a header and a body. The header contains the protocol information needed for that layer, while the body contains the data for that layer. The body of one layer contains the entire package of previously encapsulated layer, like the skin of an onion or the functional contexts found on a program stack.
When two applications exiting on two different private networks communicate across the Internet, the data packets are encapsulated down to the physical layer where they are passed to a router. Because the router isn't concerned with What 's actually in the packets, it only needs to implement protocols up to the network layer. The router sends the packets out to the Internet, where they reach the other network's router. This router then encapsulates this packet with the lower-layer protocol header needed for the packet to reach its final destination. This process is shown in the following illustration.
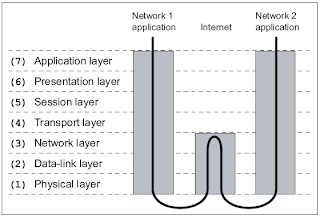
the process can be though of as an intricate interoffice bureaucracy, reminiscent of the movie Brazil, At each layer is a highly specialized receptionist who only understands the language and protocol of that layer. as data packets are transmitted, each receptionist performs the necessary duties of her particular layer, puts the packet in an interoffice envelope, writes the header on the outside, and passes it on to the receptionist at the next layer. This receptionist in turn performs the necessary duties of his layer, puts the entire envelope in another envelope, writes the header on the outside, and passes it on to the next receptionist.
each receptionist is only aware of the functions and duties of his or her layer. The roles and responsibilities are defnied in a strict protocol, eliminating he not be desirable for humans, but it's deal work for a computer. the creativity and intelligence of a human mind is better suited to the design of protocols such as these, the creation of programs that implement them, and the invention of hacks that use them to achieve interesting and unintended result. But as with any hack, an understanding of the rules of the system is needed before they can be put together in new ways.
each receptionist is only aware of the functions and duties of his or her layer. The roles and responsibilities are defnied in a strict protocol, eliminating he not be desirable for humans, but it's deal work for a computer. the creativity and intelligence of a human mind is better suited to the design of protocols such as these, the creation of programs that implement them, and the invention of hacks that use them to achieve interesting and unintended result. But as with any hack, an understanding of the rules of the system is needed before they can be put together in new ways.
What Is Networking Computer
what is networking computer??,Networking is all about communication, and in order for two or more parties to properly communicate, standards and protocol are required. Just as speaking Japanese to someone who only understands English doesn’t really accomplish much in terms of communication, computer and other pieces of network hardware must speak the same language in order to communicate effectively. This means a set of standards must be laid out ahead of time to create this language. These standards actually consist of more than just the language- they also contain the rules of communication.
As an example, when a help desk support operator picks up the phone, information should be communicated and received in a certain order that follows protocol. The operator usually needs to ask for the caller’s name and the nature of the problem before transferring the call to the appropriate department. This is simply the way the protocol works, and any deviation from this protocol tends to be counterproductive.
Network communications has a standard set of protocol, too. These protocol are defined by the Open System Interconnection(OSI) reference model.
Subscribe to:
Posts (Atom)
