The Open System Interconnection (OSI) reference model provides a set of international rules and standard to allow any system obeying these protocols to communicate with other systems that use them. These protocols are arranged in seven separate but interconnected layers, each dealing with a different aspect of the communication. Among other things, this allows hardware, like routers and firewalls, to focus on the particular aspect of communication that applies to them, and ignore other parts.
The seven OSI layers are as :
The seven OSI layers are as :
1. Physical layer
This layer deals with the physical connection between two points. This is the lowest layer, and its major role is communicating raw bit streams. This layer is also responsible for activating, maintaining, and deactivating these bit-stream communications.
2. Data link layer
This layer deals with actually transferring data between two points. The physical layer takes care of sending the raw bits, but this layer provides high-level function, such as error correction and flow control. This layer also provides procedures for activating, maintaining, and deactivating data-link connections.
3. Network layer
This layer works as a middle ground, and its key role is to pass information between lower and higher layers. It provides addressing and routing.
4. Transport layer
This layer provides transparent transfer of data between systems. By providing a means to reliably communicate data, this layer allows the higher layers to worry about other things besides reliable or cost-effective means of data transmission.
5. Session layer
This is layer responsible for establishing and then maintaining connections between network applications.
6. Presentation layer
This layer is responsible for presenting the data to applications in a syntax or language they understands. This allows for things like encryption and data compression.
7. Application layer
This layer is concerned with keeping track of the requirements of the application.
This layer deals with the physical connection between two points. This is the lowest layer, and its major role is communicating raw bit streams. This layer is also responsible for activating, maintaining, and deactivating these bit-stream communications.
2. Data link layer
This layer deals with actually transferring data between two points. The physical layer takes care of sending the raw bits, but this layer provides high-level function, such as error correction and flow control. This layer also provides procedures for activating, maintaining, and deactivating data-link connections.
3. Network layer
This layer works as a middle ground, and its key role is to pass information between lower and higher layers. It provides addressing and routing.
4. Transport layer
This layer provides transparent transfer of data between systems. By providing a means to reliably communicate data, this layer allows the higher layers to worry about other things besides reliable or cost-effective means of data transmission.
5. Session layer
This is layer responsible for establishing and then maintaining connections between network applications.
6. Presentation layer
This layer is responsible for presenting the data to applications in a syntax or language they understands. This allows for things like encryption and data compression.
7. Application layer
This layer is concerned with keeping track of the requirements of the application.
When data is communicated through these protocols, it’s sent in small pieces called packets. Each packet contains implementations of these protocols in layers. Starting from the application layer, the packet wraps these protocol in layers. Starting from the application layer, the packet wraps the presentation layer around that data, which wraps the session layer around that, which wrap the transport layer, and so forth. This process is called encapsulation. Each wrapped layer contains a header and a body. The header contains the protocol information needed for that layer, while the body contains the data for that layer. The body of one layer contains the entire package of previously encapsulated layer, like the skin of an onion or the functional contexts found on a program stack.
When two applications exiting on two different private networks communicate across the Internet, the data packets are encapsulated down to the physical layer where they are passed to a router. Because the router isn't concerned with What 's actually in the packets, it only needs to implement protocols up to the network layer. The router sends the packets out to the Internet, where they reach the other network's router. This router then encapsulates this packet with the lower-layer protocol header needed for the packet to reach its final destination. This process is shown in the following illustration.
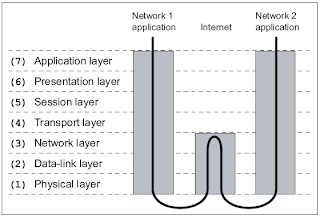
the process can be though of as an intricate interoffice bureaucracy, reminiscent of the movie Brazil, At each layer is a highly specialized receptionist who only understands the language and protocol of that layer. as data packets are transmitted, each receptionist performs the necessary duties of her particular layer, puts the packet in an interoffice envelope, writes the header on the outside, and passes it on to the receptionist at the next layer. This receptionist in turn performs the necessary duties of his layer, puts the entire envelope in another envelope, writes the header on the outside, and passes it on to the next receptionist.
each receptionist is only aware of the functions and duties of his or her layer. The roles and responsibilities are defnied in a strict protocol, eliminating he not be desirable for humans, but it's deal work for a computer. the creativity and intelligence of a human mind is better suited to the design of protocols such as these, the creation of programs that implement them, and the invention of hacks that use them to achieve interesting and unintended result. But as with any hack, an understanding of the rules of the system is needed before they can be put together in new ways.
each receptionist is only aware of the functions and duties of his or her layer. The roles and responsibilities are defnied in a strict protocol, eliminating he not be desirable for humans, but it's deal work for a computer. the creativity and intelligence of a human mind is better suited to the design of protocols such as these, the creation of programs that implement them, and the invention of hacks that use them to achieve interesting and unintended result. But as with any hack, an understanding of the rules of the system is needed before they can be put together in new ways.

No comments:
Post a Comment